In the previous post we added to the Open Badges’ DNA its first genes extracted from the blockchain. We obtained the following results:
- Everything can be represented as a Badge — everything is relationship;
- A BadgeChain is made of chained badges (not yet a blockchain);
- A BadgeChain is a like a distributed database: badges are stored all over the Internet.
- New objects can grow organically from the aggregation of badges in the BadgeChain — e.g. ePortfolios.
There are two points we have not addressed yet
- How is the BadgeChain practically stored?
- How can we trust the content of the BadgeChain?
The trustworthy BadgeChain
Can we check whether the components of the BadgeChain, Open Badges, are authentic (the issuer is the issuer, the earner is the earner, etc.) simply by looking at them, just as we would do to check whether a banknote is counterfeit? The answer is yes, and the means to do it is named cryptography. Here are the conditions to create badges that resist effective counterfeiting:
- Every participant in the network uses one or more public / private key pair;
- The public keys are used as the identities of the participants in the network.
- The private keys are used to encrypt information that can then be deciphered using the matching public keys.
- Reciprocally, the private keys are used to decipher any information encrypted by the matching public keys
The picture below illustrates the process when Alice creates a badge containing the information that will be used to verify whether it is authentic or not.
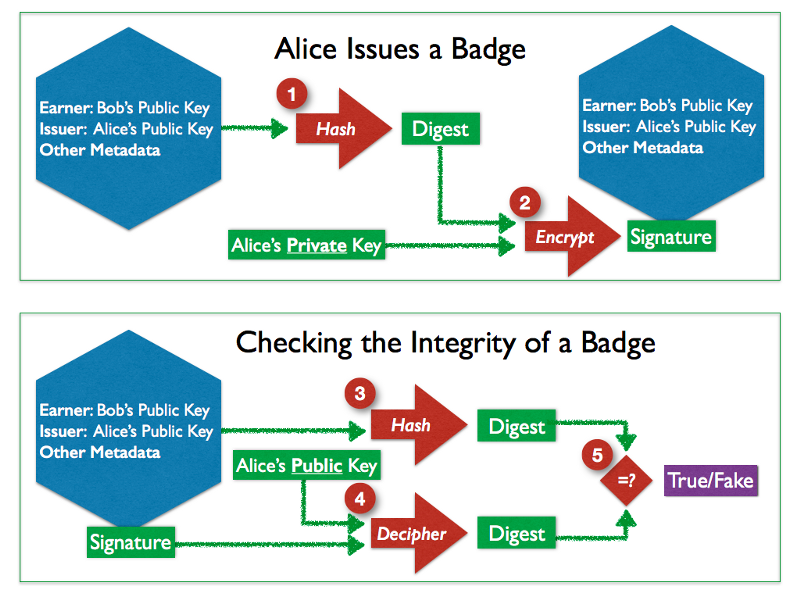
What happens when Alice creates a badge:
- For practical reasons (saving space and time) the content of the badge created by Alice is transformed into a digest, a small and unique representation of the complete badge using a public algorithm called hashing. It is as impossible to reconstruct the original badge from its digest, as it would be to rewrite an article from its summary.
- A signature is computed from the badge’s digest using Alice’s private key which is then added to the badge.
How the integrity of the badge and whether Alice is the issuer are checked:
- A digest of the badge is computed with the same hashing function used by Alice.
- The signature of the badge is deciphered using Alice’s public key which is provided by the Issuer metadata of the badge. The result should be the digest initially created, before being encrypted by Alice’s private key.
- If the two digests are different, then we can conclude that the badge is counterfeit.
Without entering into the details of cryptography, one of the properties of this kind of encryption is that it is not possible from the knowledge of public information (the public key, signature and digest) to guess what the original private key is. It is practically impossible for anybody but Alice to create a badge where she is declared as being the issuer — at least until quantum computing becomes a reality!. The down points of cryptography are that the private key must remain an absolute secret and must not be lost as it cannot be recreated (but you can save several copies in different safe places!).
The private key can be used to create one or more receiving badges, i.e. badges that will appear as the actual earners of the earned badges. This way one public/private key pair can be used to create multiple identifiers which are used to collect different types of badges.
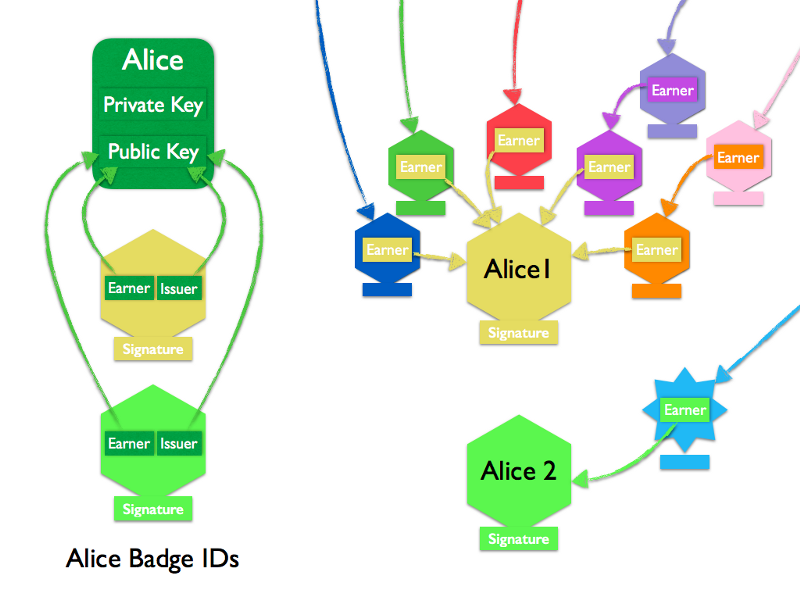
Furthermore, Alice can create multiple public/private key to keep her different identities totally separate — in the example above, the two badge identifiers make reference to the same public key, so the identities can be associated without any effort.
How is the BadgeChain stored?
To connect a badge to another badge, badges need to have an address (or an identifier that can be translated into an address) where they can be found. When Alice creates Alice 1 and Alice 2, the two genesis badges that will be used to aggregate future badges, they could be stored anywhere on the web. Alice could decide that all the badges she receives will be stored on her blog, so the location of her first genesis badge could be something like http://www.aliceblog.me/badges/alice1.png. When Bob wants to issue a badge to Alice, he can then use this address as the earner of that new badge.
Alice can then decide to store the new badge earned at http://www.aliceblog.me/badges/badgeorange.png. At a later stage if someone else wants to endorse the orange badge, the endorser will use http://www.aliceblog.me/badges/badgeorange.png as the earner of the badge.
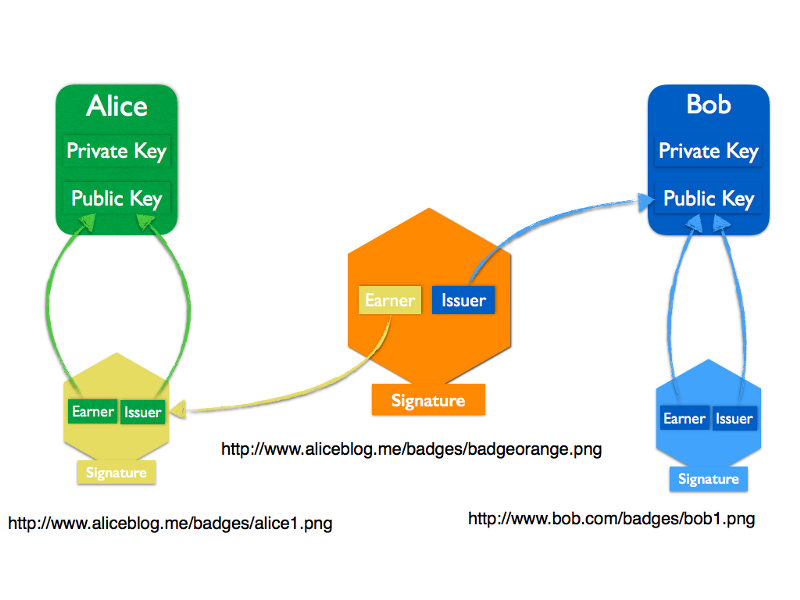
While this seems to work, in fact it does not. Let us imagine for a moment that Bob issues a first badge to Alice, then for whatever reason wants to endorse the badge he has just issued, how could he know the address before Alice has stored the badge? And when she has stored the new badge, how could Bob know its address?
The solution to this problem is twofolds:
- every badge is identified by a unique identifier or UID
- there is a means to translate a UID into a real address
For the sake of the demonstration, let us assume that each badge’s signature is unique, we could keep a table with two entries: the signature of the badge, and its real address. When we want to access the content of a badge, we look in the table for the signature to find the real location of the badge. If the holder of the badge wants to move the badges to another location, the entry in the table is changed — and if the earner wants to hide the badge, the address is erased.
A similar mechanism is used on the web to locate its content. For example, the identifier of my blog is learningfutures.eu, which is associated to the IP address 108.178.52.174. The translation of the string of characters (learningfutures.eu) into the real address on the Web is performed by a Domain Name Server or DNS. If tomorrow I decided to move my blog to another server with another IP address, I would just have to notify the DNS of the new address, and people would be able to continue to read my blog as usual.
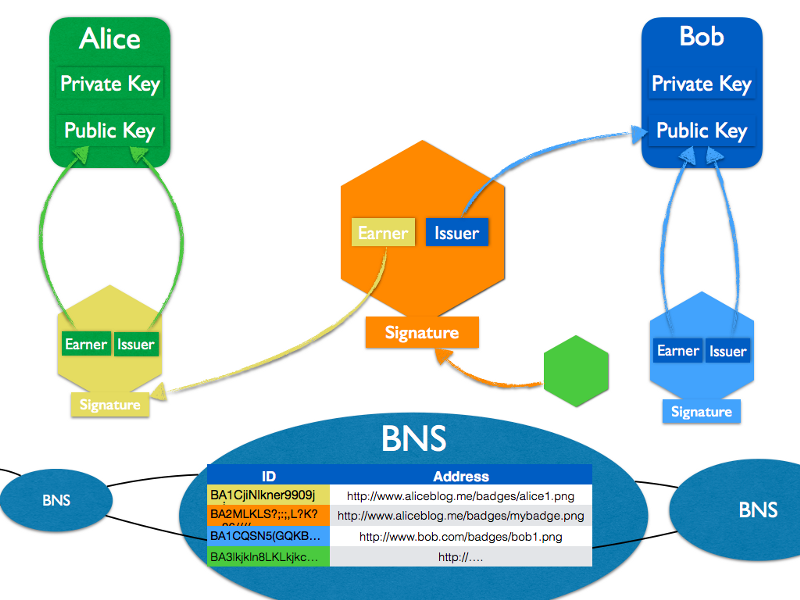
Let us call our (free) interpretation and application of the DNS mechanism to Open Badges a BNS or Badge Name Server. A BNS has several interesting features:
- The issuer enters the UID on creation of the badge — the UID column can only be written by issuers.
- The earner provides the real address of the badge after it has been accepted and stored — the real address can only be written by the earners of a badge.
- The earner can change the address of a badge (to move badges to other locations) or erase it.
- multiple copies of the BNS can be distributed among the members of the network and are synchronised by applying certain rules.
The table of the BNS could be improved by providing for each UID (the signature in our demonstration) a column with the issuer and the earner of the badge, making it easy to retrieve all the badges associated to an earner or an issuer. To revoke a badge, the badge issuer would notify the BNS to erase the entry matching the UID of the badge — after checking the authenticity of the issuer! To take into account the possibility that a badge might have been revoked, the verification mechanism of the badge integrity would start by checking that the signature of the badge is still in the BNS. If not, it would mean that the badge has been revoked.
If erasing an entry in the BNS might not seem enough to effectively revoke a badge (would not it be better if we could erase the badge altogether?) in reality it is perfectly sufficient as the original earners are facing the following dilemma:
- If they keep a copy of the badge, any person displaying the badge will see that it has been revoked
- If they erase all the copies of the badge, nobody will ever know that they once had this badge and that it is now revoked
Similarly, we cannot forbid people to create badges that would not pass the integrity test (e.g. using the public key of an issuer that is not themselves) and store those faked badges anywhere on the Web. While legal action might be sometimes necessary, once everybody understands that the only valid reference for the integrity of Open Badges is the BNS, fake badges should not have a negative impact on the trustworthiness of the BadgeChain ecosystem —as they will not be part of it. Web crawlers should be able to discover where undesired and faked badges are stored.
What have we achieved at this point?
We can create trustworthy BadgeChains that can be moved around the web. A table distributed among the members of the Open Badge ecosystem (the BNS) maintains the integrity of the BadgeChain including the revocation of badges.
There are still problems to address, in particular: as the badge earners are responsible for storing their badges, problems would arise if their storage crashed and did not have a backup to restore them — a problem unknown to blockchains with their distributed ledgers!
We still do not have a fully functional blockchain, but we are getting closer.

Follow Us